
Automate Security & IT
Streamline your IT and Security operations to automate every task and gain complete visibility from a single intelligent platform.
Live Metrics
AI Powered
Automated Actions
Next-Gen Security & IT Intelligence
AI-Powered Triage
Intelligent incident classification and routing reduces MTTR by 60% while ensuring critical issues reach the right teams.
Predictive Analytics
Machine learning models predict potential incidents before they impact your systems, enabling proactive resolution.
Enterprise Security
Built with security-first principles, featuring end-to-end encryption, audit trails, and compliance frameworks.
Seamless Integration
Connect with your existing monitoring tools, ticketing systems, and communication platforms in minutes, not months.
Complete Suite for Modern Operations
Real-Time Dashboards
Live monitoring dashboards with customizable views for different teams and roles.
Intelligent Alerting
Smart alerting with deduplication, suppression, and intelligent routing to reduce noise.
Automated Response
Runbooks and automated remediation to resolve common incidents without human intervention.
Incident Timeline
Complete audit trail with timeline view for post-mortem analysis and compliance.
Integration Hub
Native integrations with Prometheus, Grafana, PagerDuty, Slack, and 50+ more tools.
Enterprise Security
Role-based access control, audit logging, and compliance features built-in.
Our Approach
Agent-Based Metrics Collection
Lightweight agents deployed across your infrastructure continuously gather metrics from endpoints, services, and applications without interfering with your existing operations.
Non-intrusive agent deployment
Multi-protocol support
Real-time data streaming
Intelligent Analysis & Correlation
AI-powered agents analyze incoming metrics, correlate events across systems, and identify anomalies before they escalate into critical incidents.
Pattern recognition
Predictive analytics
Anomaly detection
Automated Triage & Routing
Smart routing algorithms ensure incidents reach the right team instantly with full context, suggested actions, and priority classification based on impact.
Context-aware routing
Team optimization
Priority intelligence
Security & Threat Management
Maintain compliance, ensure data integrity, and protect workloads through continuous visibility and automated defense mechanisms with minimal response time.
Real-time threat detection
Vulnerability management
Compliance and access control
How SentralOps Transforms Operations
Unified Security & Incident Dashboard
Gain a centralized view of all incidents, alerts, and agent telemetry across your entire infrastructure. Visualize health, threat levels, and response status in real time.
Real-time incident overview
Cross-system visibility
Customizable security widgets
Intelligent Alert Correlation & Automation
Reduce noise and identify true root causes with AI-driven correlation across logs, systems, and agents. Detect anomalies before they escalate.
AI-powered correlation engine
Root cause analysis
Noise reduction and prioritization
Automated Incident Response
Automate repetitive response actions using playbooks and workflows triggered directly from security events. Maintain consistency and speed in remediation.
Custom response playbooks
Secure workflow automation
Integration with external tools
Agent Telemetry & Endpoint Visibility
Monitor endpoints and agents for behavioral changes, configuration drifts, and security posture degradation — all from a unified console.
Agent heartbeat and health metrics
Configuration compliance checks
Threat surface mapping
Access Control & Policy Enforcement
Control user and system permissions with fine-grained policies, audit trails, and multi-factor enforcement. Protect against unauthorized changes.
Role-based access control (RBAC)
MFA & session management
Audit logging and policy tracking
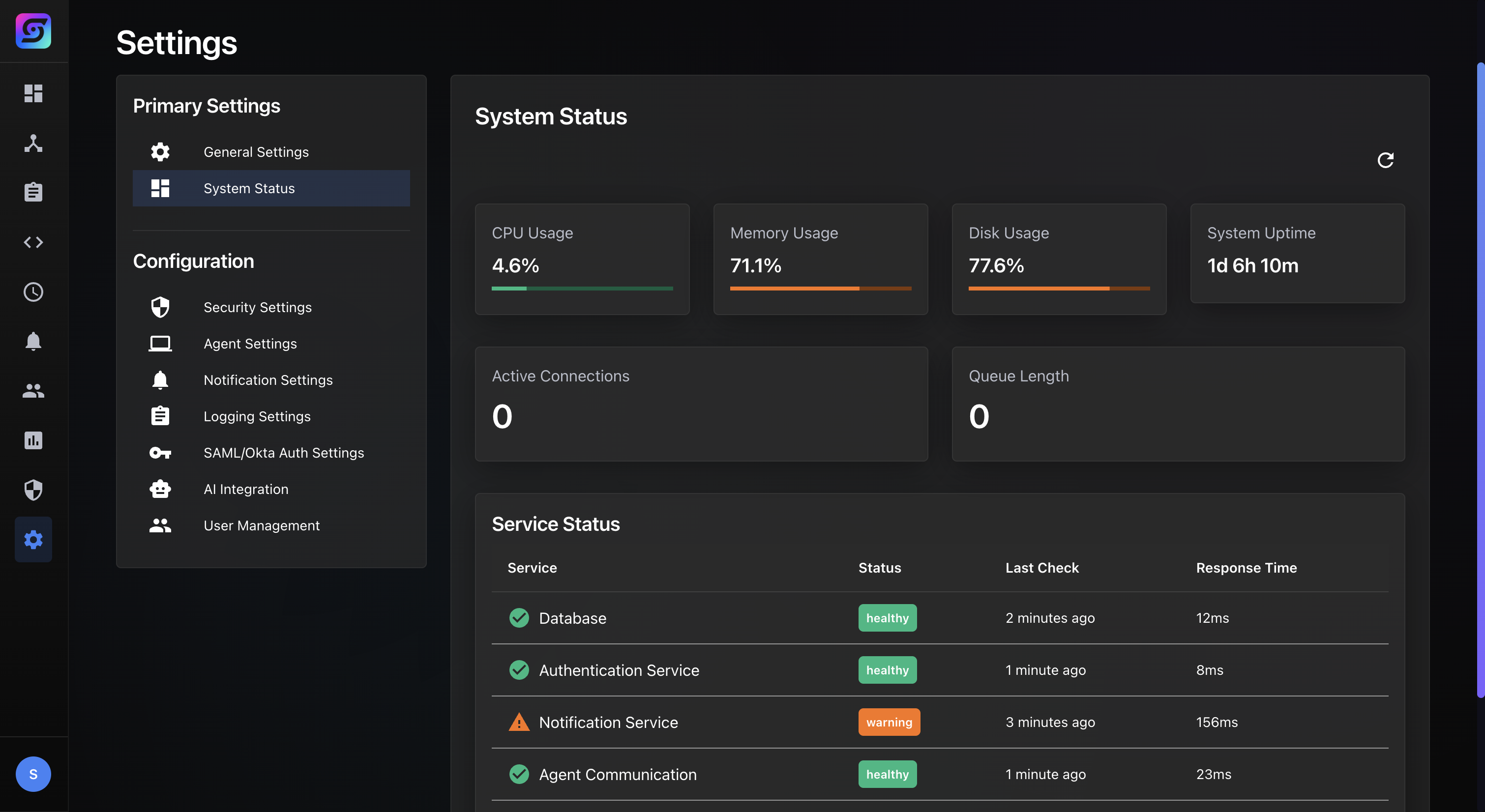
System Health & Reliability Insights
Track system uptime, service availability, and API reliability. Detect anomalies that may affect operational or security stability and get notified about the overall status.
Service uptime tracking
API latency monitoring
Anomaly detection
Seamless Integrations
AWS
Azure
Google Cloud
Grafana
Prometheus
Datadog
New Relic
Splunk
Okta
Auth0
Snowflake
Sumo Logic
CircleCI
AWS
Azure
Google Cloud
Grafana
Prometheus
Datadog
New Relic
Splunk
Okta
Auth0
Snowflake
Sumo Logic
CircleCI
AWS
Azure
Google Cloud
Grafana
Prometheus
Datadog
New Relic
Splunk
Okta
Auth0
Snowflake
Sumo Logic
CircleCI
Cisco
Fortinet
Palo Alto
VMware
Juniper
Kubernetes
Docker
Cisco
Fortinet
Palo Alto
VMware
Juniper
Kubernetes
Docker
Cisco
Fortinet
Palo Alto
VMware
Juniper
Kubernetes
Docker
PagerDuty
Slack
ServiceNow
Jira
Confluence
GitHub
GitLab
Elastic
Sentry
Opsgenie
Terraform
Asana
Zendesk
Monday.com
Freshservice
PagerDuty
Slack
ServiceNow
Jira
Confluence
GitHub
GitLab
Elastic
Sentry
Opsgenie
Terraform
Asana
Zendesk
Monday.com
Freshservice
PagerDuty
Slack
ServiceNow
Jira
Confluence
GitHub
GitLab
Elastic
Sentry
Opsgenie
Terraform
Asana
Zendesk
Monday.com
Freshservice
Why Choose SentralOps
Reduce MTTR by 60%
AI-powered triage and intelligent routing ensure incidents reach the right team faster than ever.
Proactive Operations
Agent-driven insights detect issues before they impact users, preventing downtime and outages.
Unified Visibility
Centralize all your monitoring tools and incident data in one comprehensive dashboard.
Enterprise Security
Built with security-first principles, SOC 2 compliant with end-to-end encryption.
Actionable Insights
Transform raw incident data into meaningful metrics and actionable intelligence.
Scale Effortlessly
From startup to enterprise, grow your incident management capabilities with your organization.
Security & Compliance
Security is built into every layer of SentralOps. From infrastructure hardening to application security, we follow industry best practices.
Least privilege access control
Secret scanning in CI/CD
Container image scanning
SAST/SCA security scanning
TLS encryption in transit
CSP headers and secure defaults
Frequently asked questions
- How long does it take to evaluate SentralOps?
- Our standard evaluation period is 30 days, giving you ample time to integrate and test the platform with your existing infrastructure. We provide comprehensive onboarding support during this period.
- Can SentralOps integrate with our existing monitoring tools?
- Yes, SentralOps integrates with popular monitoring stacks including Prometheus, Grafana, Alertmanager, and many other tools via our flexible API. Custom integrations are also available.
- How does data flow from our systems to SentralOps?
- Data ingestion happens via secure agents deployed on your infrastructure or via direct API connections. All communication is encrypted in transit, and we follow a least-privilege security model.
- Is SentralOps available for on-premises deployment?
- Yes, SentralOps can be deployed on-premises or in a hybrid configuration. We also offer AWS-hosted options with CloudWatch, RDS, and other managed services.
- What kind of support is available during evaluation?
- All evaluation customers receive email support with a 24-hour response SLA. Priority support with faster response times is available for production deployments.
- How does SentralOps handle sensitive incident data?
- All sensitive data is encrypted at rest using industry-standard AES-256. We implement comprehensive secret scanning, image scanning, and security scanning in our CI/CD pipeline. Access is controlled via TLS and CSP headers.
Ready to Transform Your IT & Security Management?
Request a demo and see how SentralOps can streamline your operations within minutes.
Or email us at info@sentralops.com
